Deploying an SSH Honeypot with Docker to Record SSH Login Passwords
It’s been a long time since I updated my blog. Today when I logged into the server, I found records of SSH being brute-forced, 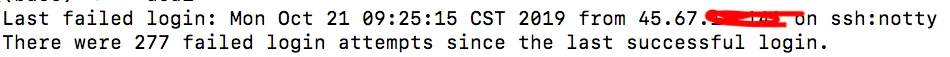, so I thought why not record the hacker’s passwords and try to reverse-login to his server. After some searching, I found there are two methods to record SSH login information: the first is to recompile OpenSSH and patch it to record SSH login passwords, and the second is to deploy an SSH honeypot using Docker to record brute-force passwords. This article introduces the second method: using Docker to record SSH brute force logs.
My environment is CentOS 7; Ubuntu differs somewhat, so you might need to adjust environment-related parameters accordingly.
Main steps:
- Change the sshd service port
- Change the default sshd service port
- Disable SELinux
- Modify sshd configuration file and restart ssh service
- Deploy SSH honeypot with Docker
- Install Docker and start Docker service
- Build the SSH honeypot Docker image and run the honeypot
Change sshd service port
Change the default sshd port
Directly edit the SSH config file /etc/ssh/sshd_config, find the line #Port 22 and change it to port 2222 here:
vim /etc/ssh/sshd_config
As shown:
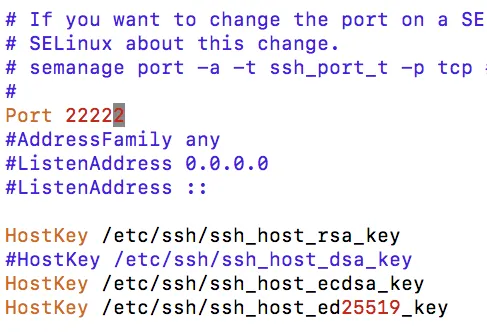
Disable SELinux
Edit /etc/selinux/config to disable SELinux:
vim /etc/selinux/config
Change to
SELINUX=disabled Then reboot the system:
shutdown -r now
Check SELinux status with
If it shows SELinux status: disabled then SELinux is successfully disabled.
Restart ssh service
systemctl restart sshd.service
If you see errors like 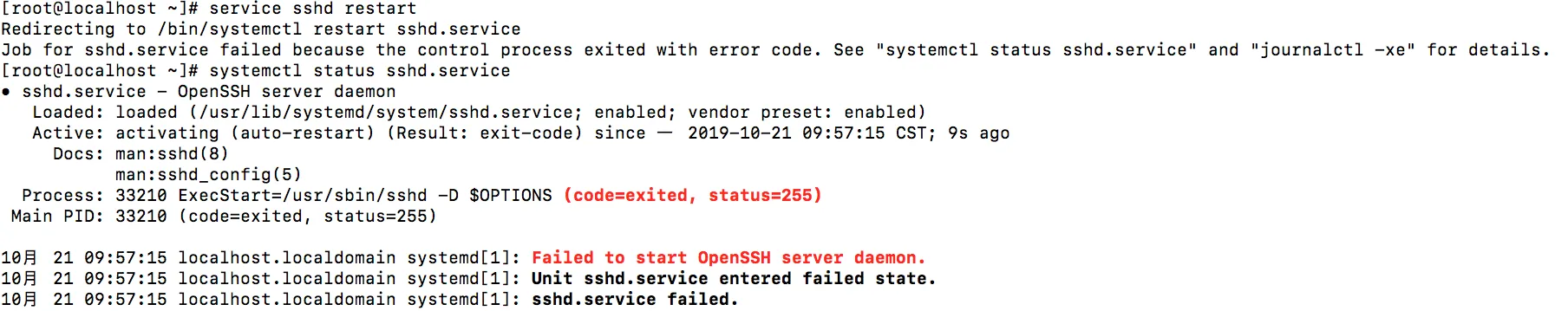
please go back and make sure SELinux is disabled.
Check SSH service status on the new port:
netstat -nlp|grep 222
 it means the sshd service port was successfully changed.
it means the sshd service port was successfully changed.
Deploy SSH honeypot Docker
Install Docker and start Docker service
yum update -y
yum install docker -y
systemctl start docker.service
Update yum and install/run Docker.
Build the first server and record information
Use the SSH honeypot Docker image from GitHub repo droberson/ssh-honeypot:
git clone https://github.com/random-robbie/docker-ssh-honey
cd docker-ssh-honey/
docker build . -t local:ssh-honepot
docker run -itd --name ssh-honeypot -p 22:22 local:ssh-honepot
Here, we build an SSH honeypot image with Docker, then map the Docker honeypot’s port 22 to the local port 22. We changed our own SSH port earlier to avoid conflict with this honeypot port.
Check local port 22 status:
netstat -nlp|grep 22
Next, check the usernames and passwords captured by the honeypot.
First, view logs via command line:
```bash
docker logs -f $(docker ps -f name=ssh-honeypot -q) | grep -v 'Error exchanging' | head -10
Second, save logs to a file for later analysis:
docker logs -f $(docker ps -f name=ssh-honeypot -q) | grep -v 'Error exchanging' | awk '{print $6, $7, $8}' >> /root/ssh_name_pass.log
From now on, analyze the recorded SSH brute-force passwords from the log file ssh_name_pass.log.
After one day, check SSH login records:
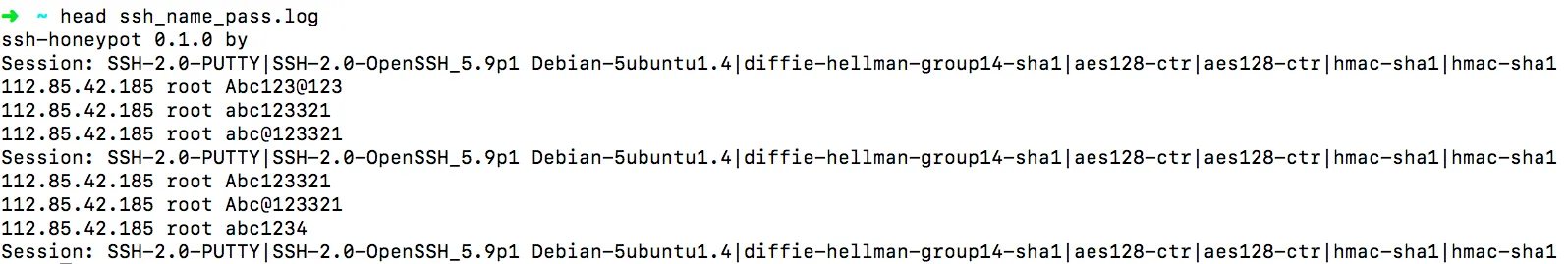
Analyze login IPs and passwords using shell commands:
cat /root/ssh_name_pass.log|grep -v ssh- |grep -v Sess|awk '{print $1}'|sort |uniq -c ##Check login IPs and counts
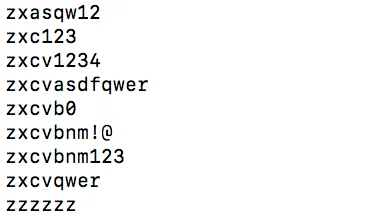
cat /root/ssh_name_pass.log |grep -v ssh-|grep -v Sess|awk '{print $3}'|sort > /root/pass.txt ###Save passwords used to login via SSH
#cd ~ && tail pass.txt
Now you know the attacker IPs and the passwords they tried.
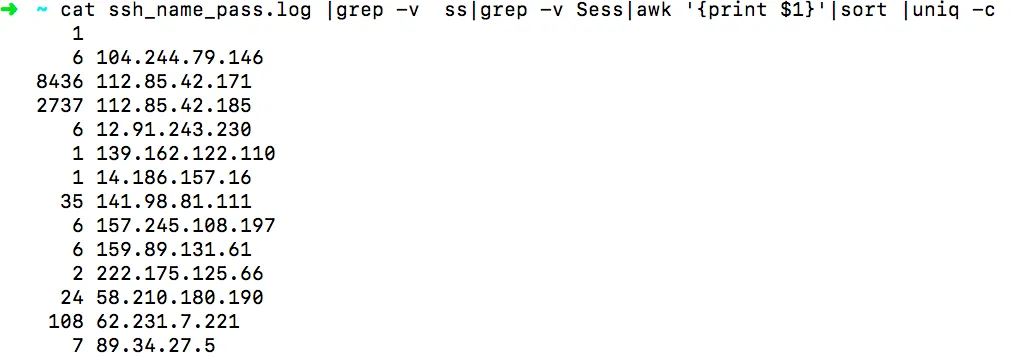
Check the login passwords:
cd ~ && tail pass.txt
Summary
That’s all for this article. It started from finding SSH brute-force attempts, then deployed an SSH honeypot using Docker to capture usernames and passwords trying to log into the server. Compared to patching OpenSSH, this is simpler and avoids recording local user information, which is a great method.
Of course, the real way to secure SSH is:
Use SSH keys and disable password login
Restrict remote port access to only local IPs via firewall/security groups
- 原文作者:春江暮客
- 原文链接:https://www.bobobk.com/en/613.html
- 版权声明:本作品采用知识共享署名-非商业性使用-禁止演绎 4.0 国际许可协议进行许可,非商业转载请注明出处(作者,原文链接),商业转载请联系作者获得授权。